Semantic Access Control, A Semantics-based Access Control Model for Open and Distributed Environments
|
The Semantic Access Control, SAC
The Semantic Access control model was created in 2002.
The fundamentals of this semantics-based access control model are the definition of several metadata models at different layers of the Semantic Web. Each component of SAC represents the semantic model of a component of the access control system. The semantic properties contained in the different metadata models are used for the specification of access control criteria, dynamic policy allocation, parameter instantiation and policy validation processes.
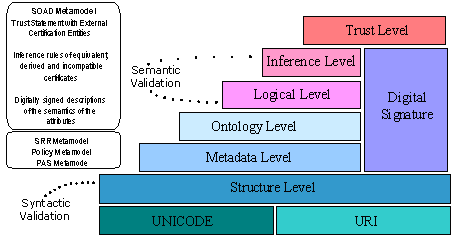
The Semantic Access Control model is based on the semantic properties of the resources to be controlled, properties of the clients that request access to them, semantics about the context and finally, semantics about the attribute certificates trusted by the access control system.
In the development of the Semantic Access Control model we have considered the operation of several independent access control systems and authorization entities. In SAC, the access control to resources is independent of their location. The identification of the user or client is not mandatory. On one hand, the client possess a set of attributes and, on the other hand, the access control to resources is based on the specification of a set of attributes that the client has to present to gain the access to them. For interoperability and security reasons, client attributes must be digitally signed (e.g., in the form of an attribute certificate) by a trusted certification entity, external to the access control management system.
The independence of the certification of attributes function is the key to the interoperability because it allows attributes to be safely communicated avoiding the necessity of being locally emitted by the system administrator. Additionally, this approach avoids the registration phase of the client, and the emission of a client attribute repeatedly for each access control system. For this approach to be secure, a mechanism to establish the trust between these access control systems and the authorization entities is required. We have addressed this problem using semantic information about the certifications issued by each authorization entity.
One of the main characteristics of the Semantic Access Control is that, opposed to traditional schemes, the attributes required to access a resource may depend on the semantic properties of the resources.
The allocation of the policy corresponding to a resource is not based on the storage structure of the resources but on the semantic properties of the resources. Of course, it is also possible to consider the structure of storage.
The approach followed in SAC enables the semantic validation of the access control criteria. SAC has been developed to facilitate the management of the access control system, while guaranteeing the simplicity, correction and safety of the system.
The Semantic Access Control (SAC) model has been implemented on the basis of a language to specify the access control criteria and the semantic integration of an external authorization entity . This language is called Semantic Policy Language (SPL) because it is based on the semantic properties of the resources to be accessed and the semantics about the context.
SPL applies traditional concepts of modularity, parameterisation and abstraction in order to provide simplicity and flexibility to the difficult task of specifying access control criteria. The modular definition of SPL policies implies the separation of specification in three parts; that is, access control criteria, allocation of policies to resources and semantic information (properties about resources and context).
Additionally, SPL makes possible the abstraction of access control components and, as a consequence, the ability to reuse these access control components. All the previous properties help the reduction of the complexity of management. Moreover, the use of semantic information about the context allows the security administrator to include relevant contextual considerations in a transparent manner, also helping the semantic validation task.
Plagiarism: There exist other works that use the term Semantic Access Control and Semantic Policy Language but applied to Grid Computing. In particular, the work from 2005 which presents "a new access control method what is called Semantic Access Control (SAC)" include text directly copied from one of the original Semantic Access Control papers published since 2002, without any reference to any of these works. Please, have a look at section 2.1 of by Junzhou Luo, Xiaopeng Wang, Aibo Song and Section 2 of
Applying the Semantic Web Layers to Access Control of the original Semantic Access Control.
You can download full texts of publications related to this semantics-based access control model:
International Journals
- "Integrating PMI Services in CORBA
Applications", (Abstract)(Full Paper)
(by Javier Lopez, Antonio Maña, Juan
J. Ortega, José M. Troya, Mariemma I. Yague),
published in Computer
Standards & Interfaces Journal, 25(4), pp. 391 - 409. 2003.
Elsevier Science.
International Conferences
- "Applying the Semantic Web Layers
to Access Control", (Abstract) (Full Paper)
(by Mariemma
I. Yagüe, Antonio Maña, Javier López and José M. Troya),
in the Web Semantic Workshop. DEXA 2003
Conference.
IEEE Computer Society Press, Prague,
September 2003.
- "A Semantic Approach for Access
Control in Web Services", (Full
Paper)
(by Mariemma
I. Yagüe & José M. Troya, ),
Euroweb 2002 Conference. The Web and the
GRID: from e-science to e-business , pp.483-494,
British
Computer Society, World Wide Web Consortium , Oxford, December
2002.
- "Secure Content Distribution for
Digital Libraries", (Abstract)(Full paper)
(by Mariemma I. Yagüe, Antonio Maña,
Javier Lopez, Ernesto Pimentel, José M. Troya, ),
Digital Libraries: People, Knowledge, and
Technology 5th Int. Conference on Asian Digital Libraries (ICADL'02),
pp.483-494,
LNCS
2555, Springer-Verlag, Singapore, December 2002.
- "Semantic Access Control Model: A Formal Specification, (Abstract)(Full paper)
(by Mariemma I. Yagüe, Maria-del-Mar Gallardo, Antonio Maña),
European Symposium On Research In Computer Security, ESORICS 2005
pp.24-43,
LNCS
3679, Springer-Verlag, Milano, Italy, September 2005.
- "EC-GATE: An Infrastructure for
DRM", (Abstract) (Full Paper)
(by Mariemma
I. Yagüe, Antonio Maña, Vicente Benjumea),IASTED Intl. Conference on Communication,
Network, and Information Security (CNIS'03)IASTED
Conferences, New York, December 2003.
- "Access Control Infrastructure for
Digital Objects", (Abstract)(Full paper)
(by Javier Lopez, Antonio Maña,
Ernesto Pimentel, José M. Troya, Mariemma I. Yagüe),
International Conference on Information and
Communications Security (ICICS'02), pp.399-410,
LNCS
2513, Springer-Verlag, Singapore, December 2002.
- "XML-Based Distributed Access
Control System", (Abstract)(Full Paper)
(by Javier Lopez, Antonio Maña,
Mariemma I. Yagüe)
Third
International Conference on E-Commerce and Web Technologies (ECWeb'02),
pp.203-213,
LNCS
2455, Springer Verlag, Aix-en-Provence (France), September 2002.
|
| |